
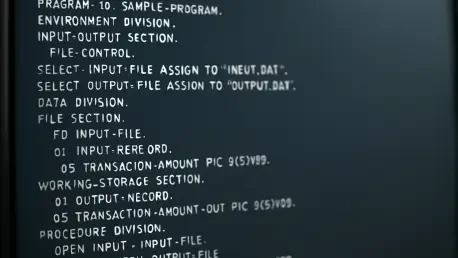
The global financial ecosystem currently rests upon a foundational layer of code that few modern engineers can read, yet it processes the vast majority of the world's daily commerce and government transactions. While many assumed that these legacy systems would eventually fade into obsolescence,

The rapid evolution of the Vietnamese telecommunications sector has reached a critical milestone as the nation transitions from basic connectivity to a sophisticated hub for edge computing and localized artificial intelligence. This transformation is driven by a strategic alliance involving VNPT,

The rapid acceleration of digital infrastructure across the African continent has transformed what was once a conversation about simple data storage into a sophisticated race for technological sovereignty and economic resilience. In 2026, the landscape of African enterprise technology no longer

The digital foundations of the global economy shifted significantly as a massive capital injection redefined the relationship between the world’s most advanced artificial intelligence and the most expansive cloud infrastructure on the planet. This monumental $50 billion investment marks a historic
The sheer magnitude of the global capital reallocation toward artificial intelligence infrastructure suggests that the industry is no longer merely a software-driven phenomenon but a full-scale industrial revolution. As 2026 unfolds, technology giants are transitioning away from the lean,

As an authority in cloud technology, Maryanne Baines has spent years evaluating the intricate tech stacks and product applications that drive modern industry. With a keen eye for how established providers like Oracle and SAP navigate the shifting tides of the digital landscape, she offers a

The sheer velocity of global digital transformation has rendered traditional, reactive maintenance models entirely obsolete for the modern data center. As enterprises shift toward 2027 and beyond, the expectation for hardware reliability has evolved from simple uptime to absolute operational

The current digital landscape reveals a striking paradox where cutting-edge defensive technologies coexist with a widespread failure to implement fundamental security measures across the global enterprise. According to the latest findings from the Unit 42 Global Incident Response Report, modern

The rapid evolution of generative artificial intelligence has forced a dramatic reckoning within the enterprise software sector, placing industry giants at a critical crossroads where traditional subscription models face an existential threat. Salesforce, long the undisputed leader in cloud-based

The rapid evolution of cloud-native ecosystems has fundamentally transformed how modern organizations design, deploy, and manage their most critical digital assets. While the shift toward containerization initially focused on the speed of delivery and the portability of code, the industry quickly
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65
ITCurated uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our Cookie Policy